Understanding what stands for Web Application Firewall, and being aware of the best practices and rules are important if you plan to work with WAFs. If you’re a developer, you will understand the importance of a WAF fairly easily. Developers work on websites and applications that are accessible to the general public. This means that they will have to deal with a lot of users and traffic. This is why a WAF is so important to an organization. It is essentially a defense system that protects your website and applications from attacks. Users who are unfamiliar with your website will be able to access it. Users who are familiar with your website will be able to access it with ease. This is why WAFs are so important. They will be able to help users access your website and applications with ease. This article will help you understand what a WAF is, the importance of a WAF, how a WAF works, and the best practices and rules of working with WAFs.
What is a Web Application Firewall?
A web application firewall is a security layer that sits between the Internet and an organization’s internal network. It basically acts like a gate to keep the bad guys out and the good guys in. It does this by examining the contents of HTTP requests and responses. It then looks for patterns that indicate malicious activity or abnormal activity.
If it detects anything suspicious, it will then stop or alter the request or response. For example, a web application firewall may detect a bad request for a slew of files. It will then alter the request to show just one of the files. This is a way for it to stop the bad guys from accessing all of the files on your server. A WAF will also look for various other patterns that indicate malicious activity.
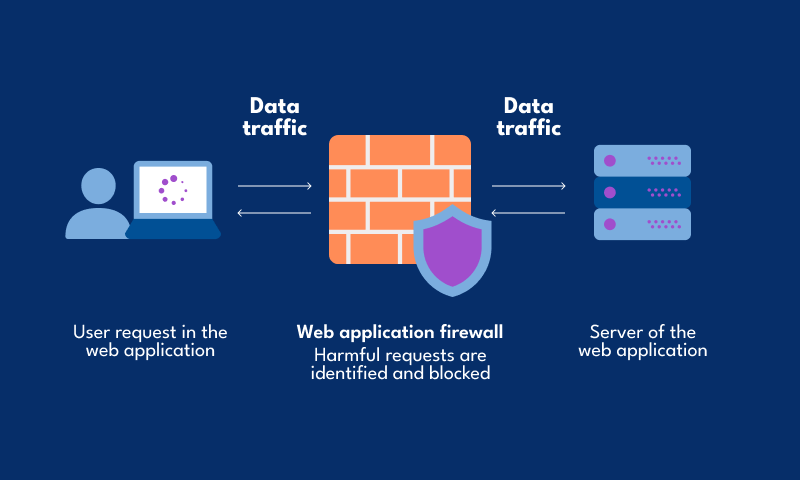
How a Web Application Firewall Works
A good way to understand the working of a WAF is by looking at what goes on when you visit a website. Let’s say you type in ‘www.yourwebsite.com’ in your browser. A request for that particular URL gets sent to the website’s server. The server then looks at the URL and sends a response. The browser receives the response and then displays the website to the user. The working of a WAF is exactly the same. It examines the URL and then looks at the response. The WAF then makes sure that it doesn’t allow any harm to come to the server. It then acts like a gate and ensures that no one gets through. It does this by looking for patterns and stopping them.
What’s the WAF false positives?
With any system, there will always be false positives. A WAF is a security layer that looks for malicious activity. It then blocks or alters the request or response if it is detected. This means that a WAF will block or alter requests that are not malicious. It cannot know for sure whether the request is good or bad. A WAF will then look for various patterns that indicate malicious activity.
One of the patterns that a WAF will look for is for HTTP requests for images. A WAF may see a request for an image and then block it. It then needs to know whether the request is related to an image or not. It then needs to look for various signs that can indicate what the request is for. For example, the request may be for an image with a specific size, file path, and extensions. A WAF then needs to understand how the request is supposed to work.
Understanding WAF Rules, RegEx and signatures
Now that we have understood what a WAF is and how it works, let us now look at some important rules that stand for a WAF. A WAF is essentially a rule-based system. It will look for various patterns and stop or alter the request or response if it is detected.
A WAF will look for various patterns and will then act like a gate to keep the visitors and hackers out. A WAF is essentially a rule-based system. It will look for various patterns and will then act like a gate to keep the visitors and hackers out. A good way to understand what a WAF does is by looking at what goes on when you visit a website. Let’s say you type in ‘www.yourwebsite.com’ in your browser. A request for that particular URL gets sent to the website’s server. The server then looks at the URL and sends a response. The browser receives the response and then displays the website to the user.
The working of a WAF is exactly the same. It examines the URL and then looks at the response. The WAF then makes sure that it doesn’t allow any harm to come to the server. It then acts like a gate and ensures that no one gets through. It does this by looking for patterns and stopping them.
WAF Rules – Best Practices
- Rule 1 – Restrict access
The first rule that a WAF needs to follow is that it has to restrict access. This means that the WAF will only allow those who should be accessing your network to access it. This is very important because it will help prevent unwanted access.
A good way to do this is by checking for various patterns that indicate who should be accessing your network. One of the patterns that a WAF will look for is for HTTP requests for images. A WAF may see a request for an image and then block it. It then needs to know whether the request is related to an image or not. It then needs to look for various signs that can indicate what the request is for. For example, the request may be for an image with a specific size, file path, and extensions. A WAF then needs to understand how the request is supposed to work.
- Rule 2 – Enforce strict rule-following
The second rule that a WAF needs to follow is that it has to enforce strict rule-following. This means that the WAF will stop or alter any request that is in violation of the rules that the WAF has set for it.
This will stop any hackers from breaching your network and stealing information. A good way to do this is by looking for various patterns that indicate what kind of requests the hackers will be making. One of the patterns that a WAF will look for is for HTTP requests for images. A WAF may see a request for an image and then block it. It then needs to know whether the request is related to an image or not. It then needs to look for various signs that can indicate what the request is for. For example, the request may be for an image with a specific size, file path, and extensions. A WAF then needs to understand how the request is supposed to work.
Tuning WAF rules
Now that we have understood what a WAF is and what rules it follows, let us now look at the third rule – which is, how to tune a WAF rule. A WAF rule is essentially a set of rules that a WAF follows. It is important to understand what these rules are and how to implement them.
One of the rules that a WAF needs to follow is that it has to be tuned. A WAF is essentially a rule-based system. This means that it will look for various patterns and will then act like a gate to keep the visitors and hackers out. It will then look for various patterns that indicate malicious activity and will then block or alter the request or response if it is detected.
A good way to tune a WAF rule is by understanding what it is supposed to do. A WAF rule is essentially a set of rules that a WAF follows. It is important to understand what these rules are and how to implement them.