With its working methodology similar to a reverse proxy, it is a globally recognized WAF capable of keeping nuisances like DDoS, XSS, and many at bay. Learn the art and science to bypass Sucuri website firewall.
About this WAF
A cloud-native solution, Sucuri WAF is a feature-rich website application firewall capable of keeping bad threats, ill-intended content, and performance-harming elements away from websites and contributing hugely towards improved speed and performance.
Other than preventing hidden and futuristic attacks, Sucuri WAF is used to encrypt the in-transit data as an SSL certificate is created automatically for every at-service firewall server and alters the DNS records. It’s designed to work seamlessly with all the leading website platforms like WordPress, Drupal, Magento, and Joomla.
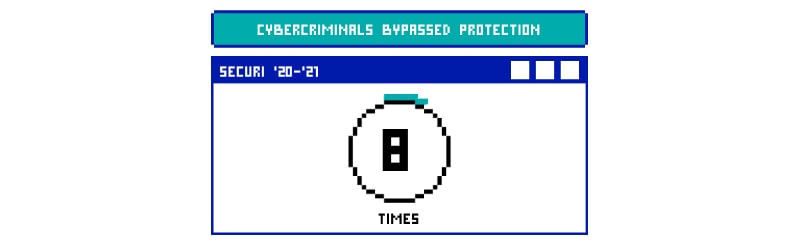
How Many Times Has The Sucuri Defense Been Bypassed in 2020-2021?
While Sucuri WAF claims to keep the website protected, hackers have found their methods to dodge its protection layer and corrupt the website hidden behind it.
As per the recent trends, talk in the community, and updates on Twitter, it was spotted out the hackers bypass the security of the Sucuri WAF defense mechanism six times in 2020-2021. That was reported cases; one must always keep scope for unreported cases or incidences that went unnoticed.
Sucuri XSS filter bypass
To ensure that XSS attacks are prevented well, Sucuri WAF uses a powerful XSS Filter.
This filter is hyperactive, and therefore, tends to provide multiple false positives too. This implies, there is a probability of blocking harmless text as well. However, bypassing it is 100% possible.
Point to be noted: The below-listed bypass firewall sucuri tricks succeeds in the case of user interaction only.
Using the Regex Reversing Technique
Based upon the previous attempts by threat actors, it was figured out that Sucuri WAF allows <a tag with href attribute. To use this as a bypassing opportunity, one should use a character that can replace the white space, generally represented as x0c.
https://www.site.com/shop.php?c=4"><a%0c href=https://www.google.com>CLICK</a>The regex technique works by finding what’s allowed in place of what’s not. It involves testing every possible filter by inserting the HTML and JavaScript codes and understanding what’s filtered out by the XSS filter.
To succeed in XSS Filter bypassing against Sucuri, one must use
https://www.site.com/shop.php?c=4"><a fooooooooooooooooooooooooooohref=https://www.google.com>CLICK</a>vector at first and then utilize a JS scheme, which will be filtered out.
Next, one must check whether or not the case-sensitive payloads and “JavaScript” with a colon as its suffix are allowed.
With this test, it could be understood that regular Sucuri expression only accepted the term “Javascript” with a “Colon” postfixed to it. To defeat it, one must use some of the key HTML unites like &sol &tab &colon &NewLine. In general, the Sucuri XSS filter filters onmouseover and on* attributes as well.
Also, every other mouse-related event handler and keyboard events are blocked. In that case, the draggable attributes of HTML5 can be of great use.
After the process, it was figured out that regex only detects the “Space” and “Forward slash” between the href attribute and a tag. So, in place of href attribute & “:”, colon; should be used.
HTML entities are usually not reflected back and can be beaten seamlessly replacing hex encodes to encode & and; signs. Put all these pieces together and you’ll be able to fully bypass the Sucuri XSS filter.
If that sounds too daunting and complex for you, there is one more way to bypass the Sucuri XSS filter. You need to find a way to bypass its attributes. On a basic level, it’s possible to break every blacklist filter. Few could be easy while few could be tough to break out of. But, breaking down is possible.
The only thing one needs is a deeper understanding of Unicode and ASCII sort of character sets and distinctive separators. Those who don’t know about separators, they are special characters analyzed as space characters.
To bypass a filter attribute, one can make it happen by finding the non-space valid separator in the given filter attribute. For instance, the [on\w+\s*] RegExp is active for filtering the on* attributes and it can be bypassed by locating the non-space valid separator.
The most suitable approach for this action is to fuzz the valid separators for every browser.
Here is a sample code wherein the 00 to ff range is fuzzed:
#python snippet
count = 0
for i in xrange(0x00,0xff):
count += 0x1
printchr(i),
print count
Begin with these inputs testing. To save the efforts invested in inputs testing, one can go by the public information and use a lookout for the separator list. Some of the most viable separators workable in multiple available browsers are as follow.
IExplorer = [0x09,0x0B,0x0C,0x20,0x3B]
Safari = [0x2C,0x3B]
Android = [0x09,0x20,0x28,0x2C,0x3B]
Chrome = [0x09,0x20,0x28,0x2C,0x3B]
Opera = [0x09,0x20,0x2C,0x3B]
FireFox = [0x09,0x20,0x28,0x2C,0x3B]
Use the separator as per the browser you’re using, alter the attribute, and bypass the Sucuri XSS filter.
How to bypass Sucuri website firewall?
It’s proved that Sucuri WAF and its protection are not enough for a skilled hacker. In case you’re wondering how to bypass it, we present you with the most viable ways.
First understand the position of Sucuri WAF in the set-up. Precisely, it sits between the client and the server.
To bypass it, the first approach is avoiding WAF’s present entirely and reaching the target. To make this happen, a lot of alternative ways and methods will be used. Secondly, the hacker needs to break down the security shield of Sucuri WAF to harm the target. Here is a detailed explanation of both approaches.
Ignoring Sucuri WAF completely
When a client tries to connect with a web server, featuring a live IP address, hackers/threat actors can bypass the protection of Sucuri WAF by sending the malicious link or injection straightway to the live IP address. If that’s not possible, one has the option to mount the server to that live IP address.
In both ways, the injection will avoid the Sucuri WAF and will reach the client.
In case you’re wondering how to get that live IP address of the server, you can use the https://www.mbtagifts.com/shop.php?c=4 site for the job. Using the mail subdomain details, one can always figure out the actual IP address of a server and corrupt it. Once you have the IP by your side, mount it to your Host file or use it directly.
https://50.28.71.142/shop.php?c=4'
https://50.28.71.142/shop.php?c=4' order by 31--+
https://50.28.71.142/shop.php?c=4' and false UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30--+
https://50.28.71.142/shop.php?c=4' and false UNION SELECT 1,2,3,4,5,concat%0a(0x4e616d65203a3a205a656e3c62723e55736572203a3a20,user(),0x3c62723e4462203a3a20,Database(),0x3c62723e56657273696f6e203a3a20,version(),0x3c62723e),7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30--+
Breaking down Sucuri WAF via routed SQL injection
In case you fail to know the IP address, the alternative way you have is to break down the Sucuri WAF and then introduce the injection/malicious elements.
Routed SQL injection is the most common procedure to use in this case. This is a scenario where there is no visible outcome after the use of”union select”. The output is not missing. It’s just not linked with the injectable query. With its help, you can simply bypass Sucuri firewall.
Key Notes
As per the recent update, Sucuri WAF has started blocking Prompt and Confirm keywords. While you try to bypass Sucuri WAF, make sure you don’t use these keywords.
Rather, use the vector, mentioned below, to bypass the Sucuri WAF.
<q oncut=\u0070rompt(2)>
"><p id=""onmouseover=\u0070rompt(1) //
A user, Mathias Karlson, claims to figure out a neat trick to doing XSS filter Sucuri WAF bypass. As per his inputs, a=”b” i is capable of carrying out a bit of CSS magic and ensuring that user interaction is inevitable.
<a id="a"href=javascript:alert(1) id="a">Click</a>In Conclusion
Sucuri WAF is just another security layer designed for added protection. However, if one knows the real server IP address, it’s easy to bypass Sucuri cache or firewall. In absence of an IP address, techniques like Routed SQL injection, regex reversing, and mounting the IP address can help you in the job.
Here you can find the complete list of Sucuri WAF bypasses throughout history