Akamai, as we all know, is an inventive piece of technology allowing end-users to boost-up web services’ performance with the help of processes like implementing rate limiting, performing caching, and bringing Web Application Firewall or WAF into action. It’s a reliable guard against DDoS attacks.
The major drawback of this useful resource is that one can easily circumvent Akamai’s protection cover by remodeling certain configurations. Hence, companies seeking the highest security are advised to learn about the Akamai Bot Protection Bypass process to leverage their protection strategies.
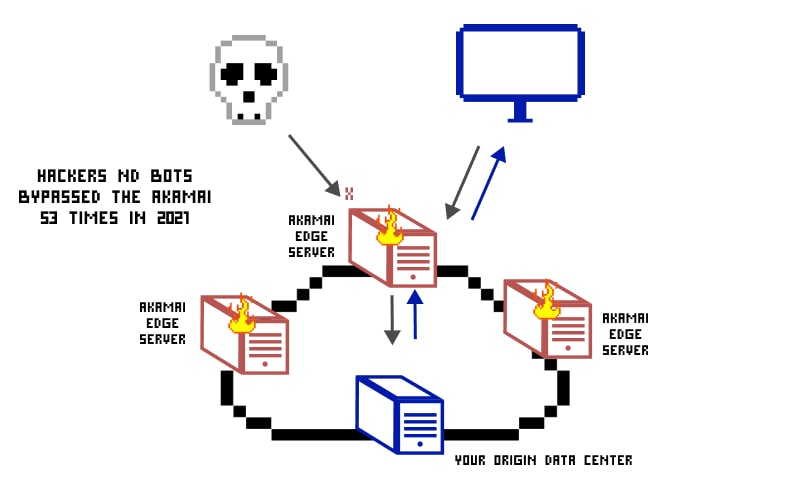
Open data on the number of attacks on Akamai
While Akamai is sure-shot way to protect the web application, it has a major drawback. One can easily circumvent Akamai’s protection cover by remodeling certain configurations. There were around 53 attacks in 2020-2021.
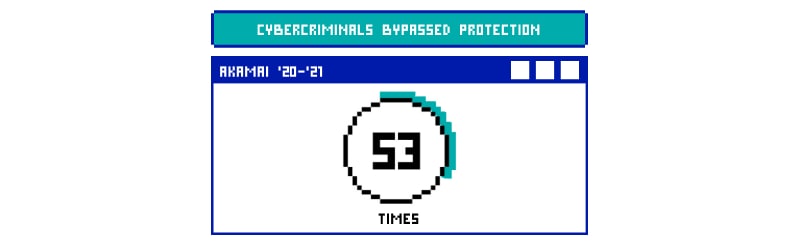
Here are a few public dumps that white/grey hat hackers made available after trying:
- People are able to bypass Akamai WAF by introducing JS comments in between a given function and related argument. Hence, companies seeking the highest security are advised to learn the process of bypassing Akamai to leverage their protection strategies.

- Even JavaScript alerts and cookie functions could help people bypass Akamai.

- Akamai WAF bypass XSS is a widely used Akamai WAF bypassing.

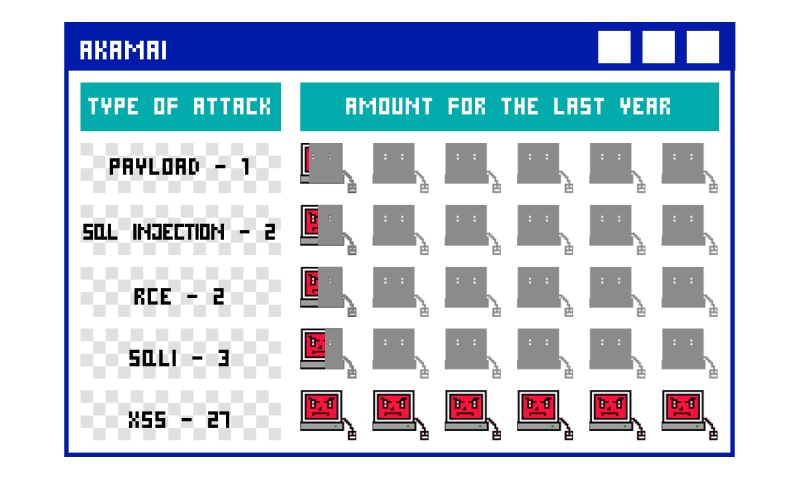
Viable Ways To Bypass Akamai
Akamai adopts multiple ways to safeguard web applications. For instance, Site Shield, Rate Limiting, and WAF. Threat actors can alter any of the deployed web-service security practices and gain authorized access. These ways are explained in detail to present a clear picture.
Strike on Origin Server
The most preferred way to avoid the Akamai protection is not passing through it. Akamai weaves a web of the distributed network between the client and the origin server. An attacker might try to find a route to reach the origin server straightforward, avoiding Akamai’s protection wall.
It’s an achievable goal Akamai doesn’t allow the origin server’s administrator to enforce incoming request limitation on every edgenodes as thousands of servers are at work and are altering their IP addresses constantly.
Attackers take the advantage of this drawback and can succeed in sending HTTP requests straight to the origin server.
Sidestep Site-Shield
Site-Shield is Akamai’s way to overcome the existing caveat in the origin server, contacting it directly using the HTTP requests. Site-Shield is placed after edgenodes and forces every HTTP request to pass through it to reach the origin server. Its presence makes HTTP request monitoring easy, moreover, it also includes caching and optimization approaches to serve cached versions of resources where available.
Sadly, attackers have figured out a way to avoid this protection wall as well. They can force edgenodes to avoid cached resources and instead, forward all the requests to the Origin for an answer, which can lead to a Denial of Service attack.
Here are the key most commonly used Akamai bot bypass procedures that attackers use to make this happen:
- Using content having zero or nearly zero TTL value
TTL stands for time to live and denotes the time for which edgenodes can hold the resource’s cached version before asking for updated resource versions. Akamai users are allowed to alter the TTL value and decide whether or not the content should feature less caching.
If attackers manage to spot the content having less or negligible TTL value, they can call that content again and again and increase the traffic for the server of content’s origin. This will lead to application accessibility.
- Through dynamic pages with unique URL or POST parameter values
Akamai has one more vulnerability and it is – Not identifying the request result when the request is dynamic and features casual yet distinctive parameter strings. The origin server will receive all these requests as hitting requests, allowing Akamai bot bypass.
- Asking for an arbitrary and exclusive page that doesn’t exist practically
Akamai is capable of tracking the presence of identified pages. When the first-page request is made, Akamai cross-checks it with Origin. Attackers take advantage of this situation and entreat exclusive pages in every request and force edgenodes to display the “page not found” message.
- Taking the help of a hidden staging server
It’s easier for an attacker to use altered edgenodes to bypass WAF or to perform Akamai bot bypass. Every Akamai client is endowed with a staging ecosystem that may have different WAF, authentication, and rate-limiting rules, which can be much simpler to attack than the original production set of rules used in WAF. Although these are staging servers for Akamai, they still point towards live sites behind the WAF. Attackers can spot these staging edge nodes by performing an nslookup of the live site and then use them to perform different attacks.
The Final Word
Akamai, when engaged, is universally used to trim down the burden that web servers carry. However, one must learn the art and science to bypass Akamai protection to recognize any hidden attempt, done by the attackers, and enhance the security. Hope this article on Akamai bot bypass gave you a quick overview of the subject.
Here you can find the complete list of Akamai bypasses throughout history