AWS WAF is an innovative resource to keep websites protected from the myriad dangers of the cyber world. While its superiority is world-known and is non-questionable, it’s not immaculate. Its restricted operability on the processed data packet sizes can act as trouble as hackers can take advantage of these loopholes and bypass the protection rendered by AWS WAF.
As an API security expert, you must be cognizant of AWS WAF bypassing possibilities so that you can fail the attempts and prevent the damage.
How many times has the AWS WAF defense been bypassed in 2020-2021?
AWS WAF claims to provide all-around protection to websites and web applications. It boasts to have the backing of some notable features like web traffic filtering. AWS WAF bot control, account takeover fraud control, and many more.
Despite that, it failed to remain safe from hackers or threat actors as a recent study has revealed that there were nearly 70 reported cases of AWS WAF bypass. This already is a huge number and we anticipate that there would be nearly the same or higher unreported cases.
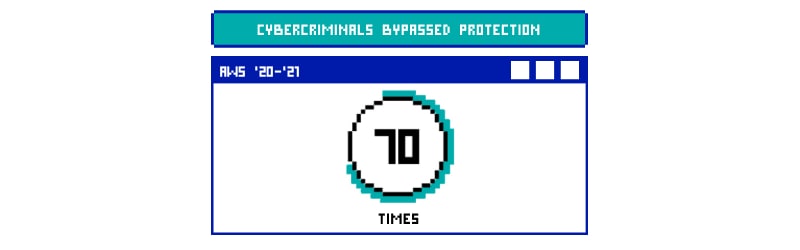
If it has already happened 70 times, it can happen one more time and you could be the next victim.
Bringing the best and verified knowledge related to ‘ how to bypass AWS WAF bypass’ at your disposal via this post.

Understanding AWS WAF Bypassing Possibilities
AWS WAF is a very famous and worldwide famous tool from the AWS security suite. Just like any other WAF, it acts as a watchman or gatekeeper for the intended web application and keeps vulnerabilities such as XSS, SSRF, SQL Injection, and many more at bay. The best part about AWS WAF is that the security or WAF rules are highly customized and can be altered as per the evolving requirements.
However, AWS WAF is not always so perfect and flawless. Certain caveats are used which any skilled hacker can bypass AWS WAF protection and hack the targeted website/web application.
Let’s get to know about those loopholes.
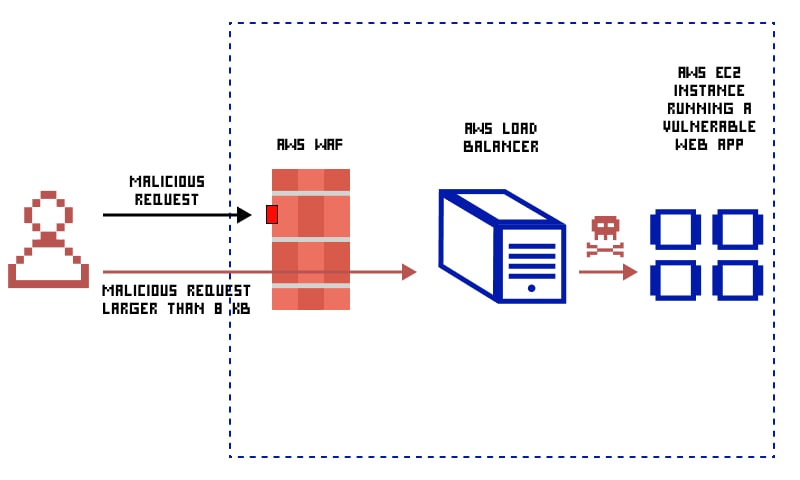
The *8K limit
Those who have a deeper understanding of AWS WAF must be knowing already that AWS WAF can process or monitor only the first 8KBs. To be very precise, only the first 8,192 bytes of the requests. Any web request, exceeding this size limit, won’t be processed or accessed by AWS WAF. Now, where does that go then? Such high-sized web requests are forwarded to the web server directly.
In case you’re wondering what impact this limit would make, pay attention to what we’re going to say next.
This limitation is well-documented and is in the public’s eye already. Now, if a hacker, intending to bypass AWS WAF, throws request traffic more than 8KB size to the targeted application, AWS WAF won’t entertain it and it will be directly forwarded to the application.
Upon receiving the traffic request, the application will process. Based on the malicious code used in the request, the hacker will be successful to carry out an SQL injection or XSS attack.
AWS WAF Enabled With CRS
AWS WAF that is enabled with CRS or Core Rule Set has been observed to be vulnerable to bypassing. CRS or Coe Rule Set is a way to overcome the 8K limitation. Using this rule, admins can pre-define the size requirements of the traffic or request.
However, this rule has a downside as well. Not every malicious request is larger than 8KB. Many validated requests or file uploads could be higher than 8KB in size and the SizeContraint rule will block them as well.
It has been observed that a website, backed by AWS WAF with CRS rules, was bypassed. It was possible by adding <! to the payload. This step will help you bypass the WAS WAF, without any script execution. It happens because of the reason that this payload is entertained as a comment by most browsers.
Characters like/ (%2F), ! (%21), % (%25), and ?(%3F) also goes unnoticed by AWS WAF and helps you in quick and seamless bypass.
How To Prevent AWS WAF Bypass?
From the above text, it’s clear that AWS WAF bypassing is possible if the hacker is skilled. If you use an AWS WAF and don’t want to see it wasted, here are the ways to prevent AWS WAF XSS bypass or any other kind of bypass.
To deal with the 8K limitation, you can take the help of the SizeContraint Rule. Adding this rule permits an ACL to take any action only when predefined size parameters are fulfilled.
One is allowed to use multiple size details in this rule. You must ensure that the rule is guiding AWS WAF to block any request equal to or more than 8,191 bytes in size. When no request, larger than 8,192 bytes, will be reaching AWS WAF, the probability of bypassing would be zero.
The ideal way to deal with CRS-driven AWS WAF bypass possibilities is to define the SizeConstraint rule as Count in place of Block. Replacing Block with Count brings desirable results only when it is assisted with further evaluation.
Conclusion
Just as the industry is finding new ways to curb the reach and impact of cyber world vulnerabilities, attackers or threat actors are working hard to bypass security solutions. Because a visionary WAF like AWS WAF can also be bypassed, we have to admit that hackers are a step ahead of the security experts.
A small vulnerability, size limitation, works as an opportunity for hackers. Hence, even if you’ve got the right kind of security solutions in place, you can be relaxed and lenient. Continual monitoring and evaluation are recommended.
Here you can find the complete list of AWS WAF bypasses throughout history