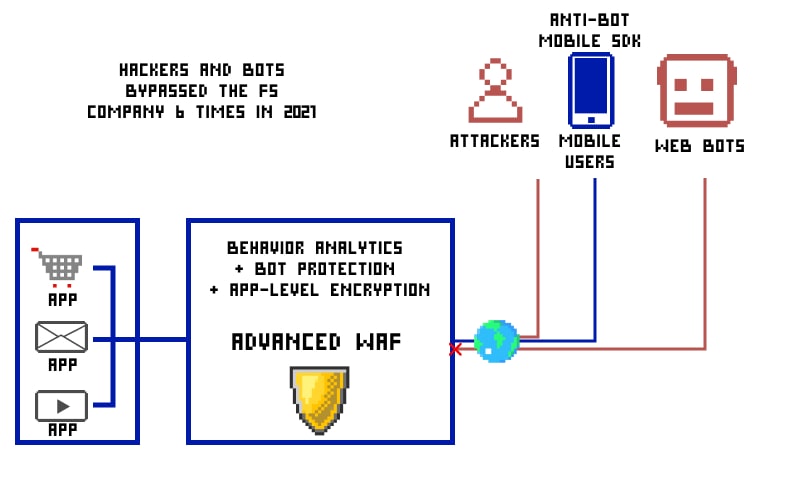
Introduction
Dedicated to making the internet and cloud a safe place to be, F5 Networks offers a wide range of security and protection solutions to businesses and individuals. The protection offered aims at multiple facets such as user access, verification, security compliances, URL protection, server defense, and so on.
In a nutshell, the organization has something or other to safeguard your digital assets and keep cyber dangers at bay. However, there are a couple of examples around us wherein threat actors have bypassed F5 Networks protection and managed to create havoc beyond our understanding.
How many times has the F5 Networks defense been bypassed in 2020-2021?
The defense mechanism that F5 Networks offers is top-notch and is hard to bypass. However, despite the high claims of providing top-notch protection, F5 Networks failed to remain unaffected by the bypassing. Threat actors and hackers remained a step ahead of the organization, managed to figure out the existing loopholes in the F5 Networks solutions, and bypassed the security wall easily.
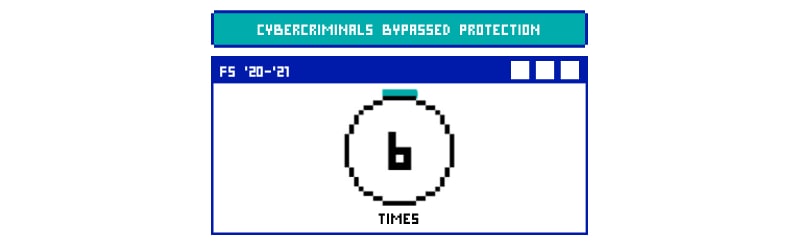
If recorded data is to be believed, around 6 times the F5 Networks security was breached or bypassed in 2020-2021.
From the GitHub community, we managed to gather information about Networks BIG-IP: Linux kernel vulnerabilities (K31026324) Nessus plugin, F5 Networks BIG-IP: PHP vulnerability (K13588), K51213246: BIG-IP APM AD authentication vulnerability, and F5 Networks BIG-IP: OpenSSL vulnerability (K15159).

What is F5 BIG IP ASM?
F5 IP ASM is the most notable offering in the domain of web threat protection and regulatory compliance. Basically, it’s a feature-rich web application firewall capable of detecting and patching the potential threats in the applications operational in different ecosystems such as customary, private, and virtual clouds.
Using a high-end algorithm, the tool does the early detection of visible and hidden vulnerabilities and helps organizations to meet the requirements to attain key mandates. It’s not a stand-alone solution. Rather, it’s one of the notable offerings of the F5 application delivery firewall solutions.
Along with BIG-IP ASM, the other offered solutions are a network firewall, SSL inspection, traffic management, DNS security, DDoS protection, and application access.
The tool attains its comprehensive security delivery via blocking access and traffic coming from suspicious sources.
Web applications are mostly secured from DDoS and SQL injection attacks while this tool is in action. Websites came into being using the latest technologies like Google Web Toolkit and AJAX widgets are compatible with the tool.
How to bypass the client on F5 BIG IP ASM?
As mentioned above, F5 BIG IP ASM bypass is possible and has already happened before. One of the most talked-about bypassing incidents was the BIG-IP APM AD authentication vulnerability CVE-2021-23008. It was identified as the KDC (Key Distribution Center) spoofing flawed and caused a great sensation.
Let’s understand how it worked and what was the process that made it work.
The problem was found in the APM – the software solution being used for managing the user access flow. Hacker was utilizing a spoofed AS-REP to enter the APM AD, i.e. Active Directory of BIG-IP. AS-REP is an authentication-related response for Kerberos services. This response should be shared or sent to a nicked KDC or Kerberos KDC connection. In its absence, it can also be forwarded via an AD server which has been compromised.
Using this KDC spoofing vulnerability (called CVE-2021-23008), any threat actor can skip security checks and affect crucial workflows. It was strong enough to go around the Kerberos security deployment, permitting the hacker to control the Access Policy Manager. It even lets threat actors reach the admin console in a few scenarios.
Steps followed to BIG-IP APM AD were:
- Creating a false KDC and accessing the username essential to gain access to the targeted F5 Networks services.
- Create a user profile in the falsified KDC and use it to perform the AD access control of BIG-IP APM.
- Taking over client-DC talks and diverting it to the counterfeit KDC.
- While AS exchange is taking place, the attacker will return the AS_REP request linked with the attacker-owned password and false KDC key.
- The attacker then returns random TGS_REP during TGS exchange.
- End-user will consent to the forged AD authentication without the application exchange.
How to prevent F5 BIG-IP APM bypassing?
Bypassing security solutions is not acceptable and should be fixed immediately.
When this vulnerability was spotted F5 took immediate action and released a list of recommended remedial actions.
The list mentioned the vulnerable versions of BIG-IP APM. People or organizations who were using the vulnerable version were provided with a patch and needed guidance to prevent threat actors from harming them. Keep in mind that CVE-2021-23008 is non-fixable in 11.5.2 – 11.6.5 versions.
In a few versions, auto-version update was the only solution needed to eliminate the issues while few demanded extended efforts like BIG-IP APM access policy reformation and system access management method audit plus improvement.
- As far as APM access policy reformation is concerned, one can utilize multi-factor authentication and apply host-level authentication constraints in addition to it.
- The BIG-IP system requires AD authentication by default. However, instead of this, you may deploy a remote authentication option, mentioned in the User Directory. you must ensure picking up a remote authentication backed by the power of SSL.
- One must watch out for the access control procedure followed in Kerberos at each step and identify any unexpected action in the early stage. For instance, AS_REQ resources requests should only be accepted. Also, the absence of TGS_REQs is an alarming situation. Wireshark is a useful tool to figure this out.
- Make sure the Kerberos protocol implementation is not completed without the validation and should be completed with the help of a keytab or password. This makes KDC spoofing tougher than usual and keeps the exploitation odds on the lower side.
- Services that are not driven by the service tickets must be searched thoroughly for the authentication logs to keep the dangers at bay.
How is the F5 WAF bypass possible?
It has been found out that F5 WAF bypass is possible by using the commands like “rev” & “printf” for command substitution functionality in Bash shell. You may give it a try and let us know if it works.
Here you can find the complete list of F5 WAF bypasses throughout history