WAFs are designed to protect web applications from external threats by filtering, monitoring, and blocking HTTP(S) traffic. However, they may not be as effective at protecting APIs, which use different protocols and data formats such as JSON. In the example described in the article, the attack involves appending JSON syntax to SQL injection payloads, which most WAFs are unable to parse. This demonstrates the limitations of WAFs in protecting against attacks that involve non-standard protocols and data formats.
API security is an important consideration for organizations that rely on APIs to access and exchange data. While WAFs can provide some level of protection, they may not be able to fully protect against all types of threats. It is important for organizations to implement additional security measures such as proper authentication and authorization, input validation, and regular testing to ensure the security of their APIs, and use specific API security solutions.
According to cybersecurity company Claroty, the attack involves appending JSON syntax to SQL injection payloads that WAFs are unable to parse. Most WAFs are able to detect SQLi attacks, but by prepending JSON to SQL syntax, these attacks go unnoticed by the WAF. Claroty’s technique successfully worked against WAFs from vendors such as Amazon Web Services (AWS), Cloudflare, F5, Imperva, and Palo Alto Networks, all of whom have released updates to support JSON syntax during SQL injection inspection.
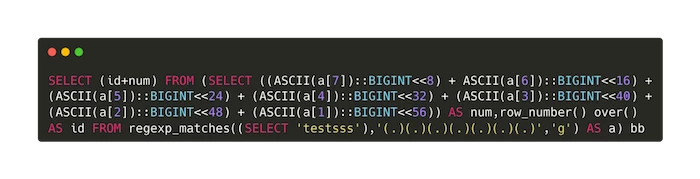
The original WAF bypass payload looks like this:
This new bypass method is especially dangerous as more organizations continue to migrate business and functionality to the cloud. Attackers using this technique could access a backend database and use additional vulnerabilities and exploits to exfiltrate information via either direct access to the server or over the cloud.
It is important to note that the WAF bypass method described in the article has been successfully demonstrated to work against WAFs from various vendors, including Amazon Web Services (AWS), Cloudflare, F5, Imperva, and Palo Alto Networks. However, it is not necessarily universal and may not work against all WAF vendors or configurations. It is also worth noting that the vendors mentioned in the article have since released updates to support JSON syntax during SQL injection inspection, which may mitigate the effectiveness of this bypass method. It is important for organizations to stay up-to-date on the latest security threats and to ensure that their WAFs are properly configured and updated to protect against these types of attacks.
It’s important for organizations to stay up-to-date on the latest security threats and to ensure that their WAFs are properly configured and updated. This includes supporting JSON syntax during SQL injection inspection and regularly testing the effectiveness of the WAF. Additionally, implementing other security measures such as regular patching, user training, and network segmentation can help to further protect against these types of attacks.
It is likely that we will see more universal WAF bypasses in the future that are able to bypass WAFs for different data formats and protocols. In 2023, we may see more attacks targeting formats like JSON, XML, and Base64, as well as protocols such as REST and SOAP, GraphQL, and WebSocket. These types of attacks can be particularly effective as they can bypass traditional security measures that are designed to protect against more commonly used protocols and data formats.
To protect against these types of threats, it is important for organizations to stay up-to-date on the latest security threats and to implement additional security measures such as proper authentication and authorization, input validation, and regular testing. It is also important for WAF vendors to continuously update their products to support a wider range of protocols and data formats and to stay ahead of emerging threats.
Subscribe for the waf-bypass newsletter to be in touch with the latest WAF bypass techniques and exploits.
Reference: https://claroty.com/team82/research/js-on-security-off-abusing-json-based-sql-to-bypass-waf